Interface Gallery & User Flows
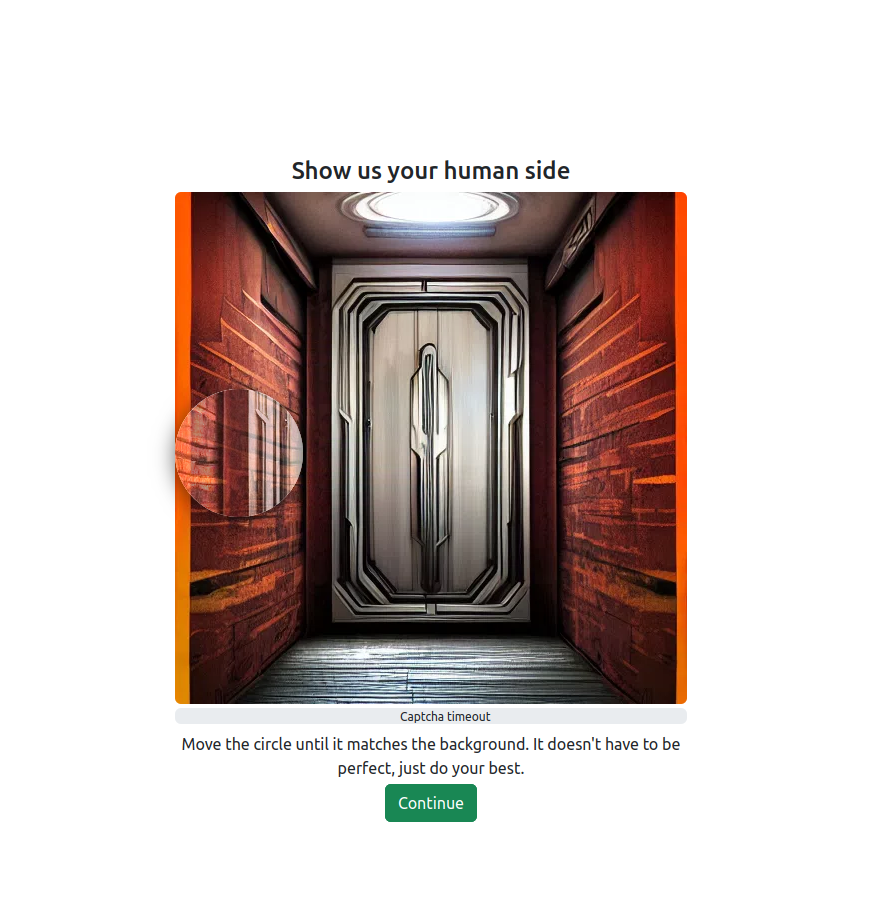
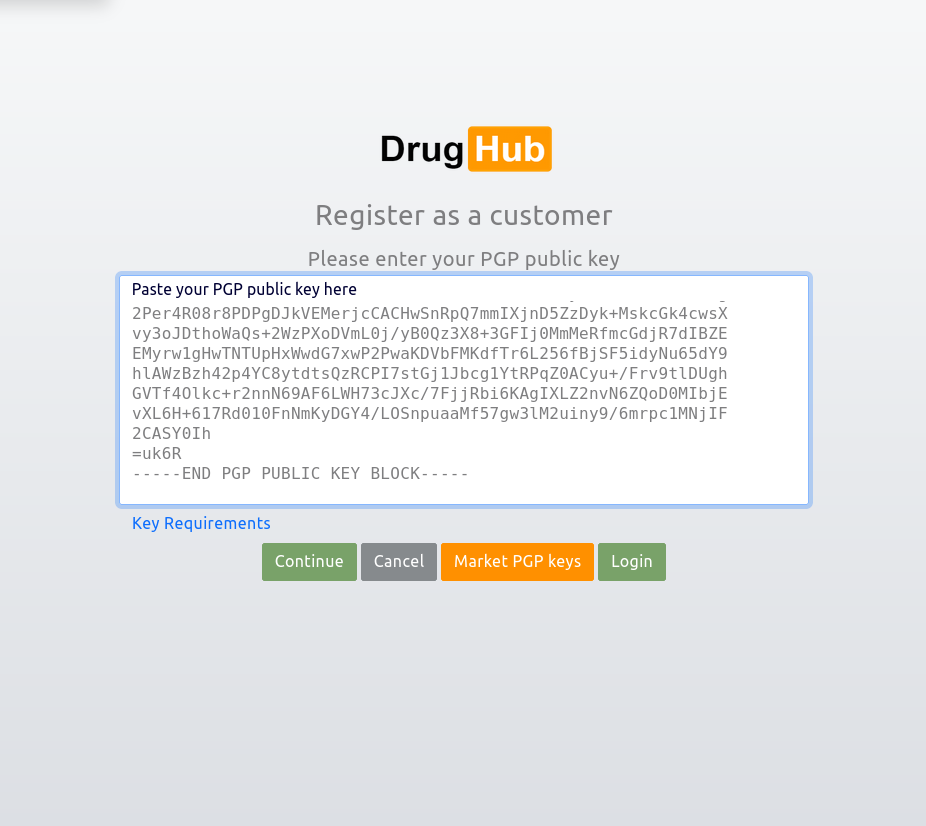
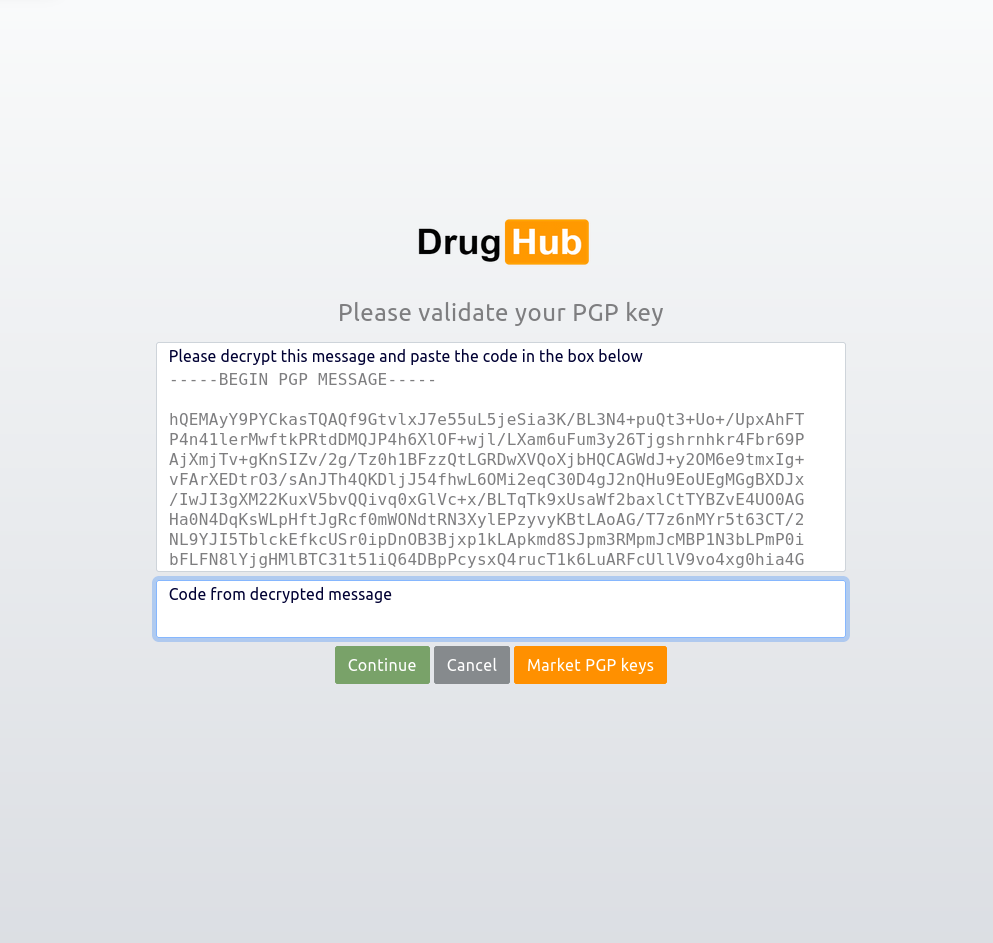
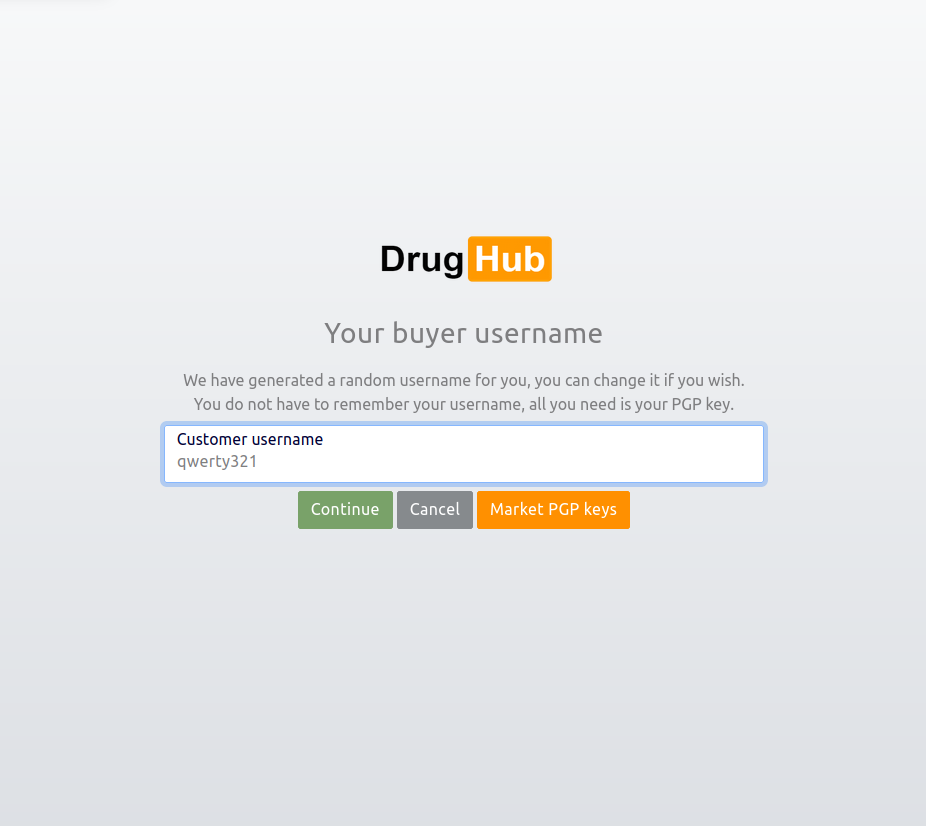
Screenshots highlight each stage of the access and interaction process, from CAPTCHA usability tests to full dashboard simulations. Each image corresponds to UX benchmarks we document.
Drughub Market. The name you trust in darknet trading. Since 2023, we've processed thousands of orders with zero major incidents. What sets us apart? Real security. Not marketing fluff. XMR-only payments. No Bitcoin tracking. PGP authentication mandatory. 2FA on every account. Our Lab Verification Program covers 90% of all listings - third-party tested for purity and accuracy. Looking for verified Drughub links? You're in the right place. We maintain multiple mirrors, rotate them regularly, and sign everything with PGP. Phishing? Not on our watch.
View Verified Research LinksDrugHub Market uses passwordless PGP authentication. No passwords to steal. Your DrugHub identity is tied only to your cryptographic keys. This DrugHub security feature reduces breach risks and speeds up login.
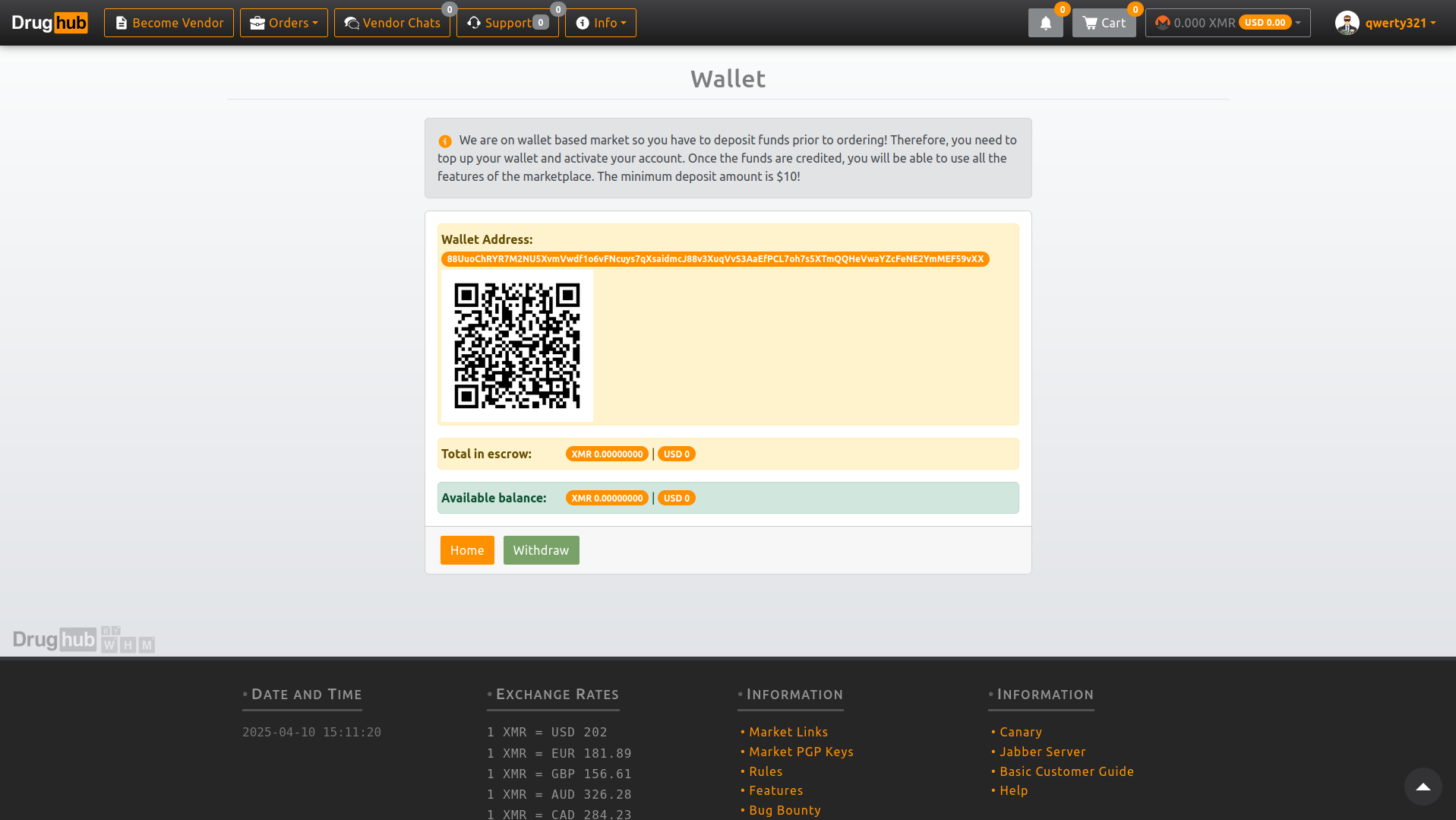
DrugHub Market is XMR-only. No Bitcoin. Monero's privacy features make DrugHub transactions untraceable. DrugHub escrow uses 2-of-3 multisig - your funds stay safe until delivery confirmed.
DrugHub Market rotates mirrors constantly. Every DrugHub link is PGP-signed. Phishing attempts fail because DrugHub users verify signatures before accessing. Real DrugHub mirrors only.
DrugHub Market was built by the White House Market team. That legacy of security defines DrugHub. Encryption best practices. Vendor trust systems. Privacy-first design. DrugHub continues this tradition.
DrugHub Market uses 2-of-3 multisig escrow. Your DrugHub funds never sit in a hot wallet. Disputes? DrugHub moderators review evidence and decide fairly. DrugHub has zero exit scam history.
DrugHub Market support responds in under 10 minutes. Use DrugHub's built-in PGP messaging or Jabber/XMPP for secure contact. Every DrugHub conversation is end-to-end encrypted.
Each step of the access process is evaluated using UX benchmarks and Web Vitals. From CAPTCHAs to cryptographic verification, our focus is on balancing usability, accessibility, and uncompromising security.
Measured for accessibility and resistance to automation bypasses.
Onboarding friction analyzed across different key management tools.
Challenge–response mechanisms benchmarked for both speed and resilience.
Provisioning speed and stability tested under various network conditions.
Transaction flows and dashboard usage reviewed for accessibility and consistency.
Our lab performs multi-layer audits: application security, network defense, and cryptographic resilience. We align our findings with W3C, MDN, and WAI accessibility standards to ensure security does not undermine usability.
Vendor workflows are studied for fairness, accountability, and trust-building. Our findings focus on how user experience and security interact in multi-user environments.
Collateral systems tested for effectiveness in ensuring accountability and discouraging fraud.
Research into inventory tools, payout automation, and performance analytics for vendor-side efficiency.
Studies show how visibility, trust scores, and performance reviews influence long-term ecosystem health.
All mirrors included in our reports are cryptographically verified and regularly tested for uptime, accessibility, and resilience against phishing.
Screenshots highlight each stage of the access and interaction process, from CAPTCHA usability tests to full dashboard simulations. Each image corresponds to UX benchmarks we document.




